
Blog

You Deserve IT Services Shaped to Your Needs
For any business to succeed, it needs to exhibit some degree of empathy toward its audience. Otherwise, the services and products they offer will be less likely to meet the priorities and needs that its targets are experiencing.
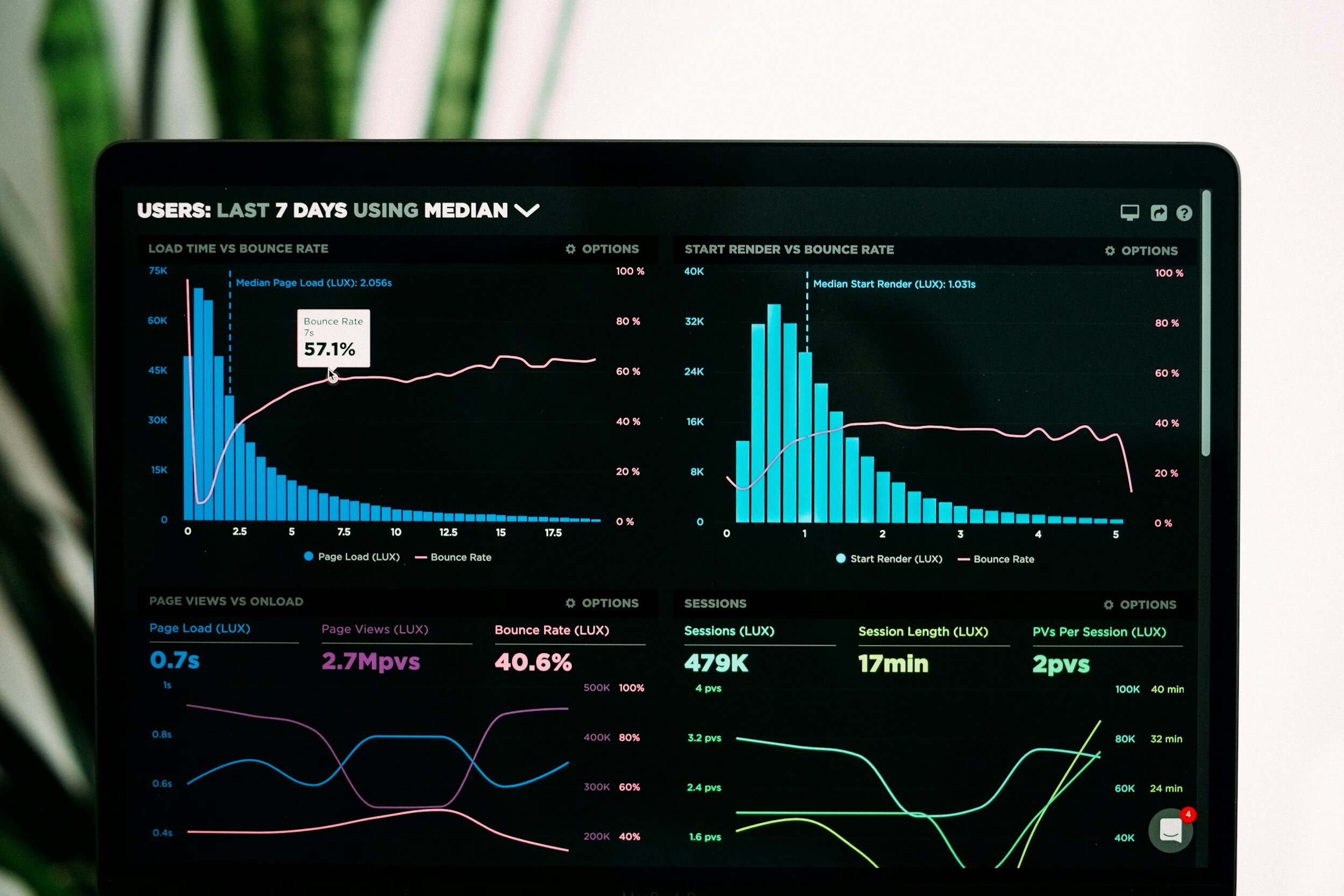
3 IT Metrics to Pay Attention To
Any business can benefit from data and use it to improve its operations. This is especially the case where information technology is involved. By collecting the right metrics, you can better evaluate your business IT’s performance and identify areas for improvement.
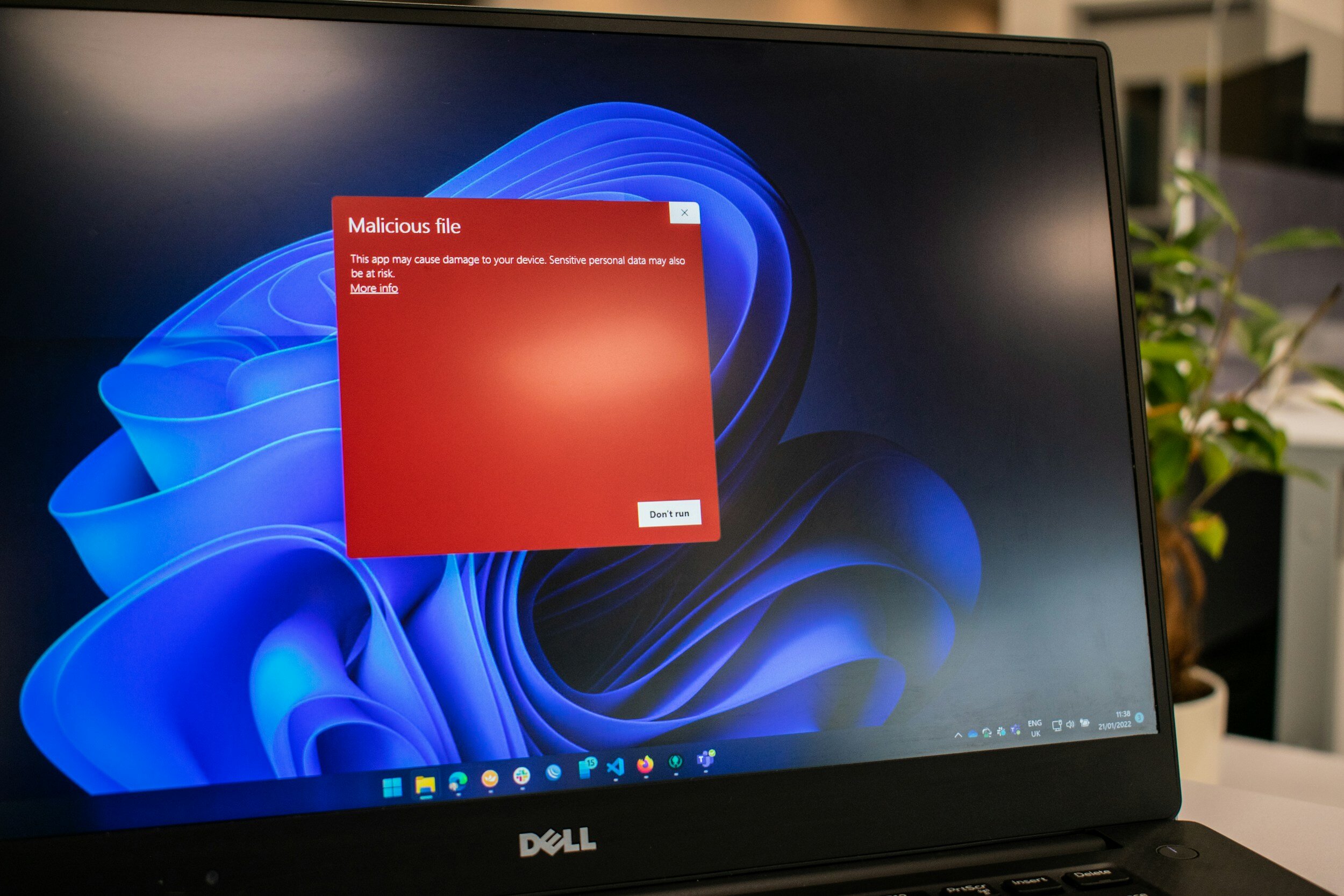
XLoader Android Malware Runs in the Background and Steals Your Data
Mobile malware isn’t common, but it’s growing increasingly more so. You may have heard of a malware called XLoader, which has been used to victimize people in over seven countries.

Did You Know? Big Tech Companies Don’t Care About Your Data Privacy
How important do you consider security for your personal and private data on your web-connected accounts? If you don’t think about it often, you should be.

Here are the Basics of the 3-2-1 Backup Rule
The 3-2-1 rule is a pretty standard reference for data backup and disaster recovery, but what does this rule actually entail?

Three of the Most Helpful SaaS Applications Out There
Software is an important part of any business’ toolset, and for small businesses, Software as a Service, or SaaS, is the most cost-effective way to take advantage of it.

Tip of the Week: Making Your Network VoIP-Friendly
We could go on and on about the benefits of using Voice over Internet Protocol (also known as VoIP) for your business telephone needs. However, it is important that you do everything you can to prepare your network for this kind of utilization.
